Losses exceed tens of millions of dollars: UXLINK security incident vulnerability analysis and stolen funds tracking
On September 23rd, UXLINK was attacked due to a leak of its multi-signature wallet private key. The attacker minted UXLINK tokens and sold them for over $11.3 million. The Beosin security team conducted vulnerability analysis and fund tracing for this attack, and share their findings below:
Event Review
The UXLINK contract's private key was leaked, resulting in the attacker's address being added as a multi-signature account for the contract and removing all other existing multi-signature accounts. Furthermore, the contract's signature threshold was reset to 1, allowing only the attacker's address to sign to execute contract operations, giving the attacker complete control over the contract. Subsequently, the attacker began issuing additional UXLINK tokens and selling them for profit.
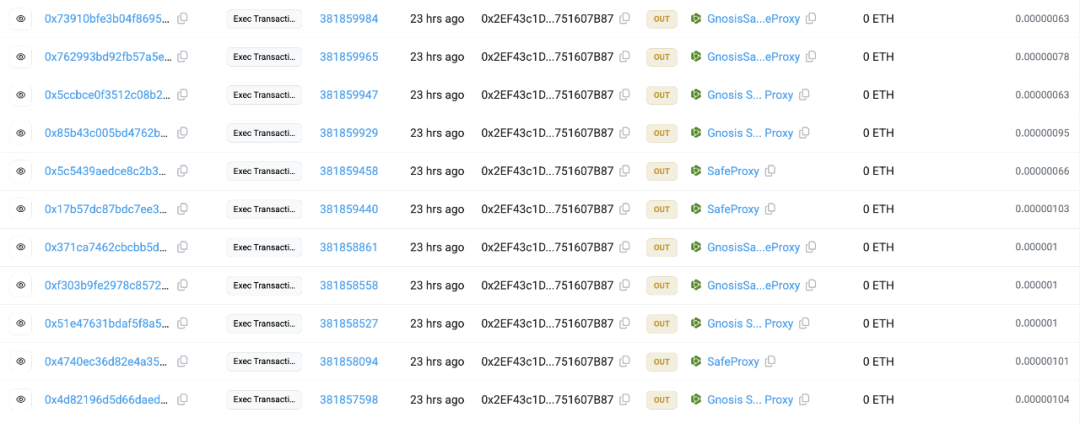
The attacker issued five additional tokens. The three token receiving addresses, 0xeff9cefdedb2a34b9e9e371bda0bf8db8b7eb9a7, 0x2ef43c1d0c88c071d242b6c2d0430e1751607b87, and 0x78786a967ee948aea1ccd3150f973cf07d9864f3, exchanged UXLINK tokens for ETH and DAI through currency exchange, transfer, and cross-chain storage, and stored them on the ETH chain address.
Stolen Funds Tracking
The following is an analysis by the Beosin security team on the main flows of funds in this security incident:
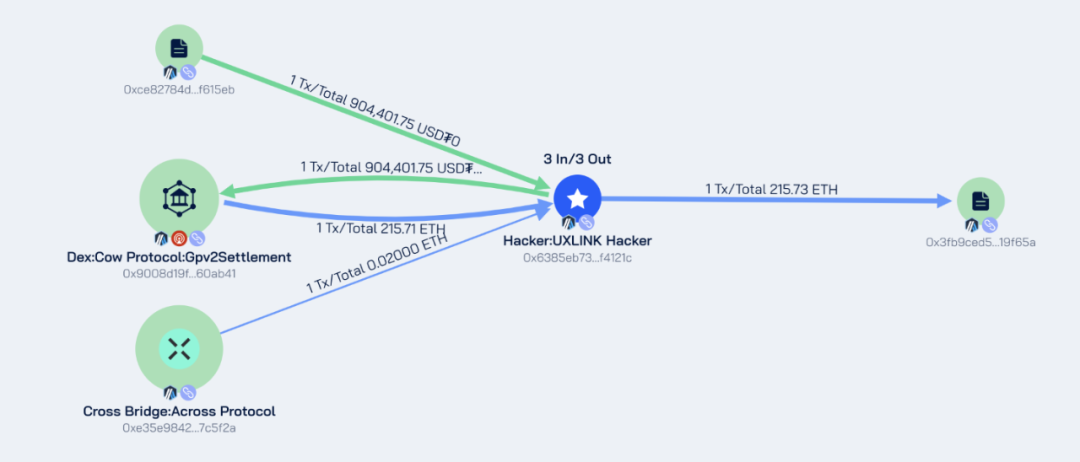
ARBITRUM CHAIN
Hacker address: 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c
Stolen address: 0xCe82784d2E6C838c9b390A14a79B70d644F615EB
Approximate amount stolen: 904,401 USDT
After stealing the funds, the hacker converted 904,401 USDT into 215.71 ETH and transferred the ETH to the Ethereum address 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c via cross-chain.
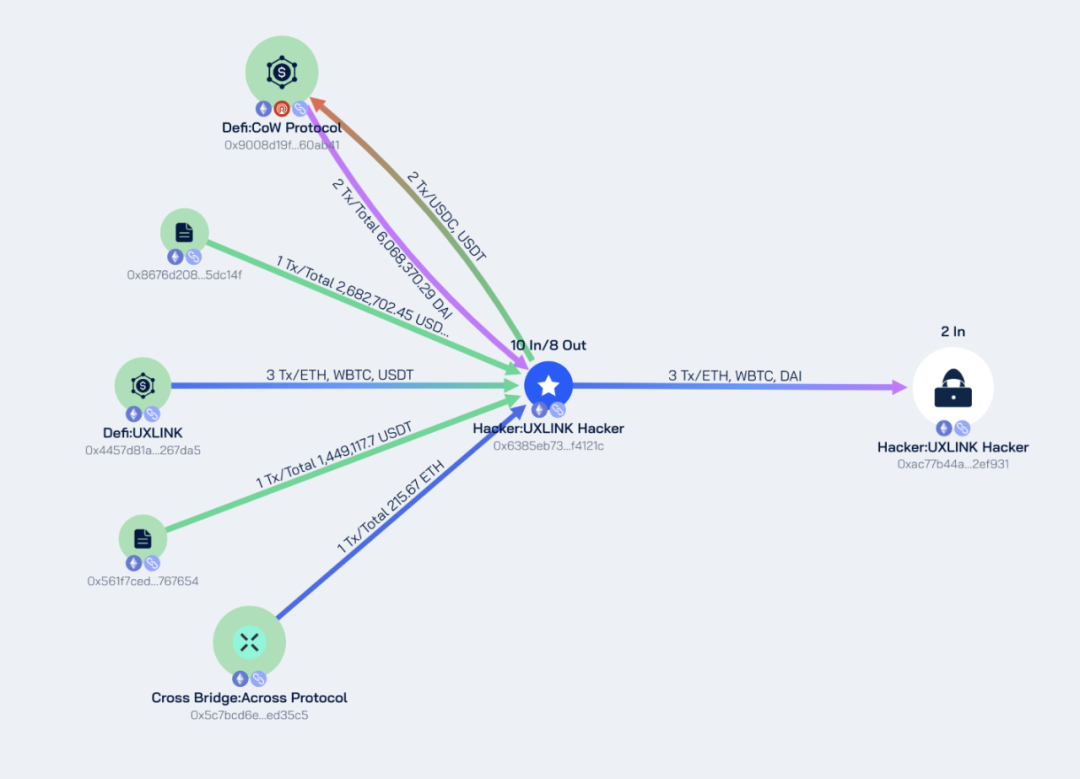
Ethereum chain
Hacker address: 0x6385eb73fae34bf90ed4c3d4c8afbc957ff4121c
Stolen addresses: 0x4457d81a97ab6074468da95f4c0c452924267da5, 0x8676d208484899f5448ad6e8b19792d21e5dc14f, 0x561f7ced7e85c597ad712db4d73e796a4f767654
Approximate stolen funds: 25.27 ETH, 5,564,402.99 USDT, 3.7 WBTC, 500,000 USDC
After stealing the funds, the hacker exchanged 5,564,402.99 USDT and 500,000 USDC into 6,068,370.29 DAI, and finally transferred the funds to the address 0xac77b44a5f3acc54e3844a609fffd64f182ef931. The current balance of this address is: 240.99 ETH, 6,068,370.29 DAI, and 3.7 WBTC.
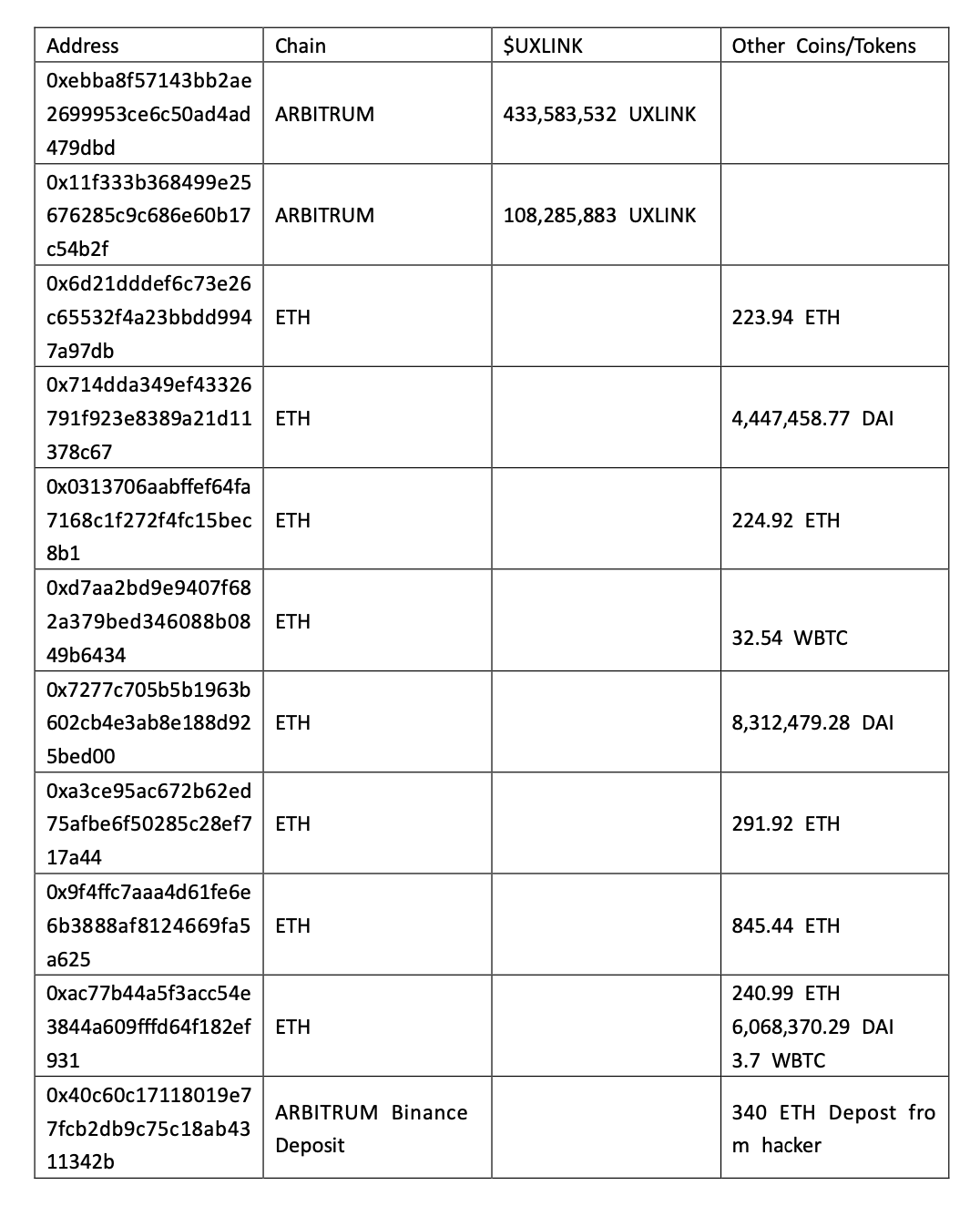
The main capital flows of Ethereum and Arbitrum are shown in the figure below:
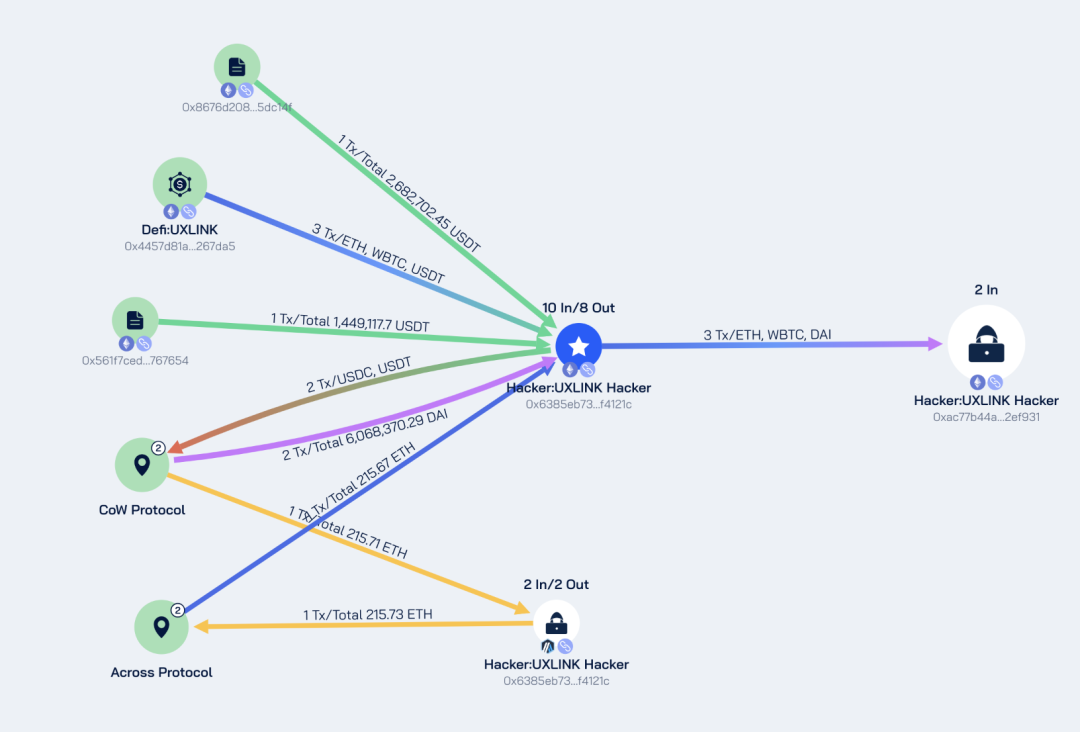
According to Beosin Trace analysis, all stolen funds are still stored in multiple addresses of the attacker.
Beosin Trace has blacklisted all addresses associated with the attacker and is continuing to track them. The following is the current balance of the attacker's related addresses:
You May Also Like

MAXI DOGE Holders Diversify into $GGs for Fast-Growth 2025 Crypto Presale Opportunities

Bank of Canada cuts rate to 2.5% as tariffs and weak hiring hit economy
