In-depth analysis of Hyperlane: a permissionless cross-chain protocol that connects more than 150 blockchains
Author: Ryan Yoon, Yoon Lee | Tiger Research
Key Points
-
True permissionless deployment: Unlike competitors that require approval processes or whitelists, Hyperlane allows any developer to instantly deploy and connect to different chains without gatekeepers, creating an access model that is fundamentally different from other interoperability protocols.
-
Flexible, modular security: While other bridge protocols use fixed security models, Hyperlane’s Interchain Security Module (ISM) allows applications to configure their own security requirements (from basic validator signatures to multi-layer verification), enabling both fast small transactions and highly secure asset transfers on the same infrastructure.
-
Developer-first architecture: Hyperlane’s TypeScript SDK, CLI tools, and comprehensive documentation lower the technical barriers to cross-chain integration, enabling inter-chain messaging through simple APIs without complex custom implementations.
1. The turning point of blockchain connectivity
The blockchain ecosystem is moving from isolated development to true interconnectivity. Instead of building closed environments, projects are increasingly looking to integrate within a wider network.

However, most integrations today remain manual and fragmented. New projects must negotiate directly with each bridge or interoperability provider - which often incurs high costs, delays, and management overhead. This creates structural barriers to participation even for technically advanced teams and ultimately hinders the scalability of the entire ecosystem.
This challenge is not new. In the early 1990s, companies operated their own separate internal networks (intranets) with their own rules and access permissions. Cross-network communication was possible but required time-consuming technical coordination and mutual authorization.
The turning point came with the introduction of standard protocols such as HTTP and TCP/IP, which enabled open, permissionless access to a unified internet. These standards laid the foundation for the digital revolution by replacing complexity with simplicity, unleashing exponential growth and global participation.
The blockchain industry now faces a similar inflection point. To unlock its next phase of innovation, it must move beyond fragmented, permission-based integrations toward standardized, permissionless connectivity. Lowering barriers to entry is critical to broad participation and innovation across the ecosystem.
2. Hyperlane’s solution: permissionless connectivity
2.1. License-free and open source
As mentioned earlier, new projects have historically faced significant barriers when joining existing blockchain ecosystems. Integrating with a bridge or interoperability protocol typically requires a complex approval process — including manual review, technical integration assessments, and security audits. Even after passing these checks, projects are often saddled with high integration costs, making connectivity prohibitively expensive.
Hyperlane solves these structural limitations through a permissionless architecture - a fundamentally different model that allows any project to connect freely. Under this approach, there is only one requirement: compatibility with a supported virtual machine (VM) environment - such as Ethereum/EVM, Solana/SVM, or Cosmos/CosmWasm. Once this condition is met, integration can proceed without a complex approval process.
As a result, the barrier to entry for blockchain projects has been significantly lowered. What used to take months to accomplish can now be done instantly once technical compatibility is met. However, the question remains: how does permissionless integration actually work?
To answer this question, let’s look at a real-world example involving Web3 developer Ryan. Ryan is building a new project called Tiger that runs its own mainnet. Currently, users on the Tiger chain are limited to the Tiger ecosystem and cannot interact with other blockchains. However, users want to bring assets from Ethereum into the Tiger chain, as well as from the Tiger chain to other chains to unlock more liquidity. In order to achieve this, Ryan must connect the Tiger chain to multiple blockchain networks.
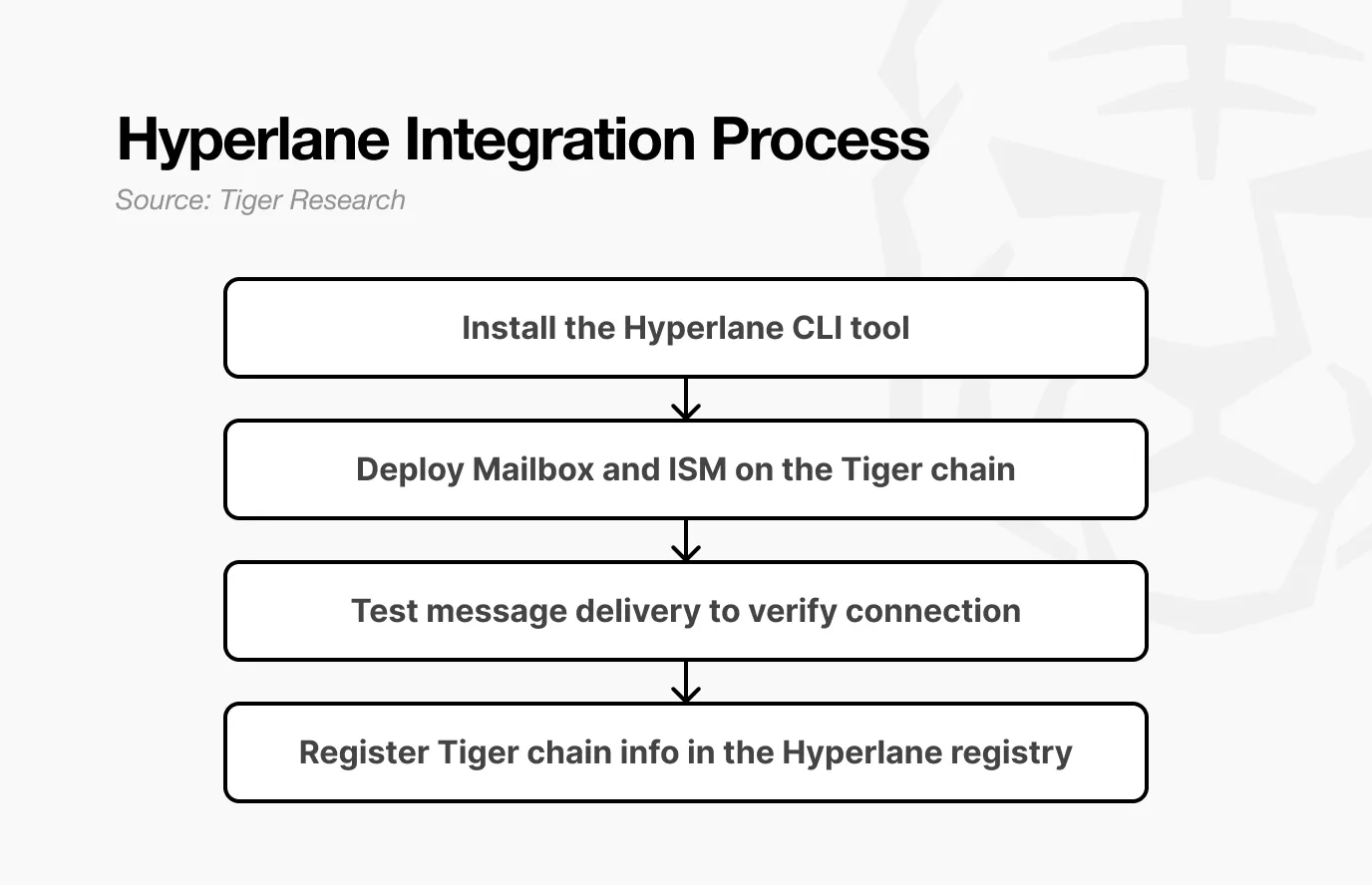
Step 1: Install Hyperlane CLI
As a first step, Ryan installed the Hyperlane CLI tool to set up the chain integration environment. The process was simple—he simply ran “npm install @hyperlane-xyz/cli” in the terminal. Since the tool is open source, no prior approval or registration is required. This ease of use highlights the core value of Hyperlane’s permissionless architecture.
Step 2: Deploy Mailbox and ISM
Next, Ryan deployed two core components directly to the Tiger chain: Mailbox (a contract that enables message transmission between blockchains) and Interchain Security Module (ISM) (used to verify the authenticity of each message). Both components are open source and publicly available, allowing developers to integrate them on their own terms. Once these elements are in place, the system can be tested.
Step 3: Test messaging to verify connectivity
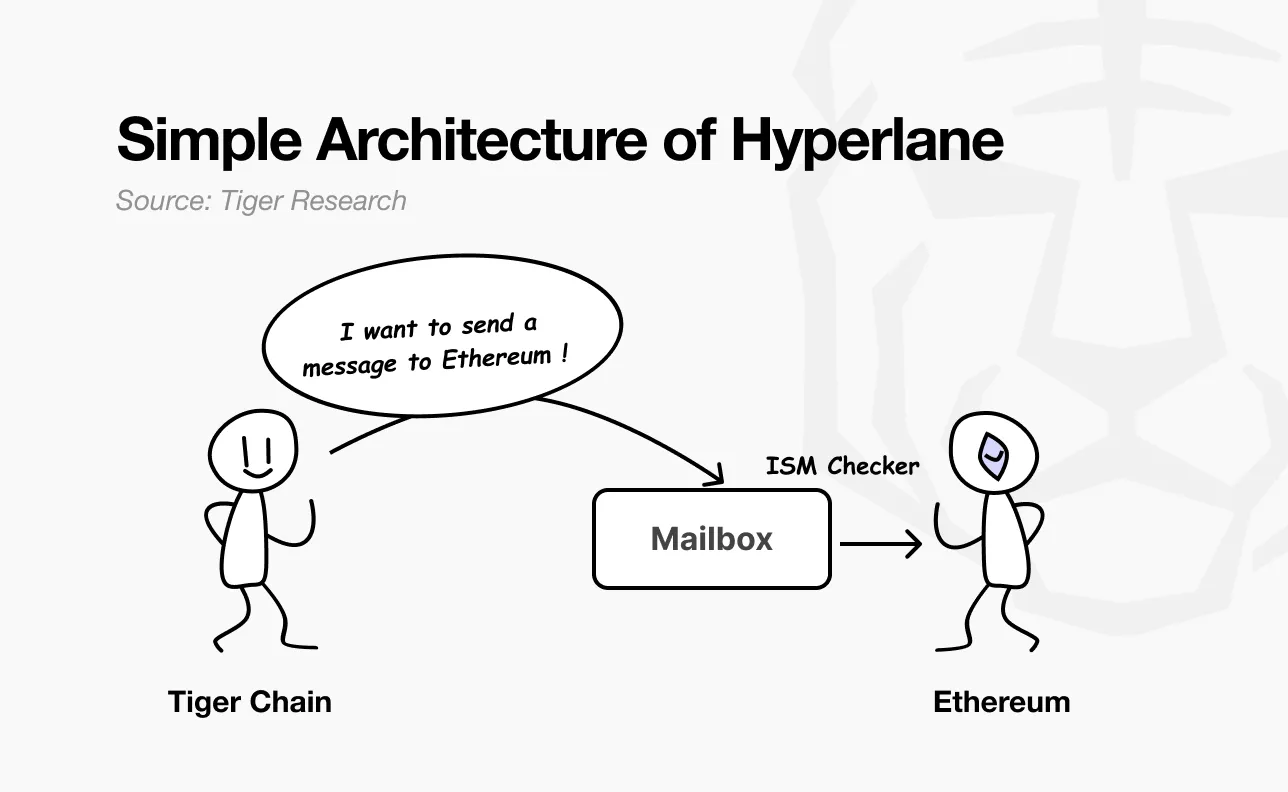
In the third step, Ryan sent a test message from the Tiger chain to Ethereum to verify that the transfer was successful. The "message" here is not a simple text string - it is a specific execution command: "Transfer 100 TIGER tokens to Ethereum address 0x123...". The transfer process is as follows:
-
Tiger Chain initiates a message to transfer 100 $TIGER tokens to Ethereum
-
Hyperlane validator verifies the message and signs it
-
The relayer passes the signed message to Ethereum
-
ISM on Ethereum verifies the message and releases 100 $TIGER tokens to the recipient
As long as both the source and target chains have Mailbox installed, no additional configuration is required. The message is transmitted, verified, and executed. A successful test confirms that the two chains are properly connected.
Step 4: Register on the public registry
In the final step, Ryan registered the connection details of the Tiger chain in the Hyperlane registry. The registry is a GitHub-based public directory that aggregates information about all connected chains, including identifiers such as domain IDs and mailbox addresses. The purpose of this public list is to ensure that other developers can easily find the information they need to connect to the Tiger chain. It functions much like a phone book - once registered, anyone can look up Tiger and initiate communication. With this one registration, the Tiger chain gains access to the full network effects of the Hyperlane ecosystem.
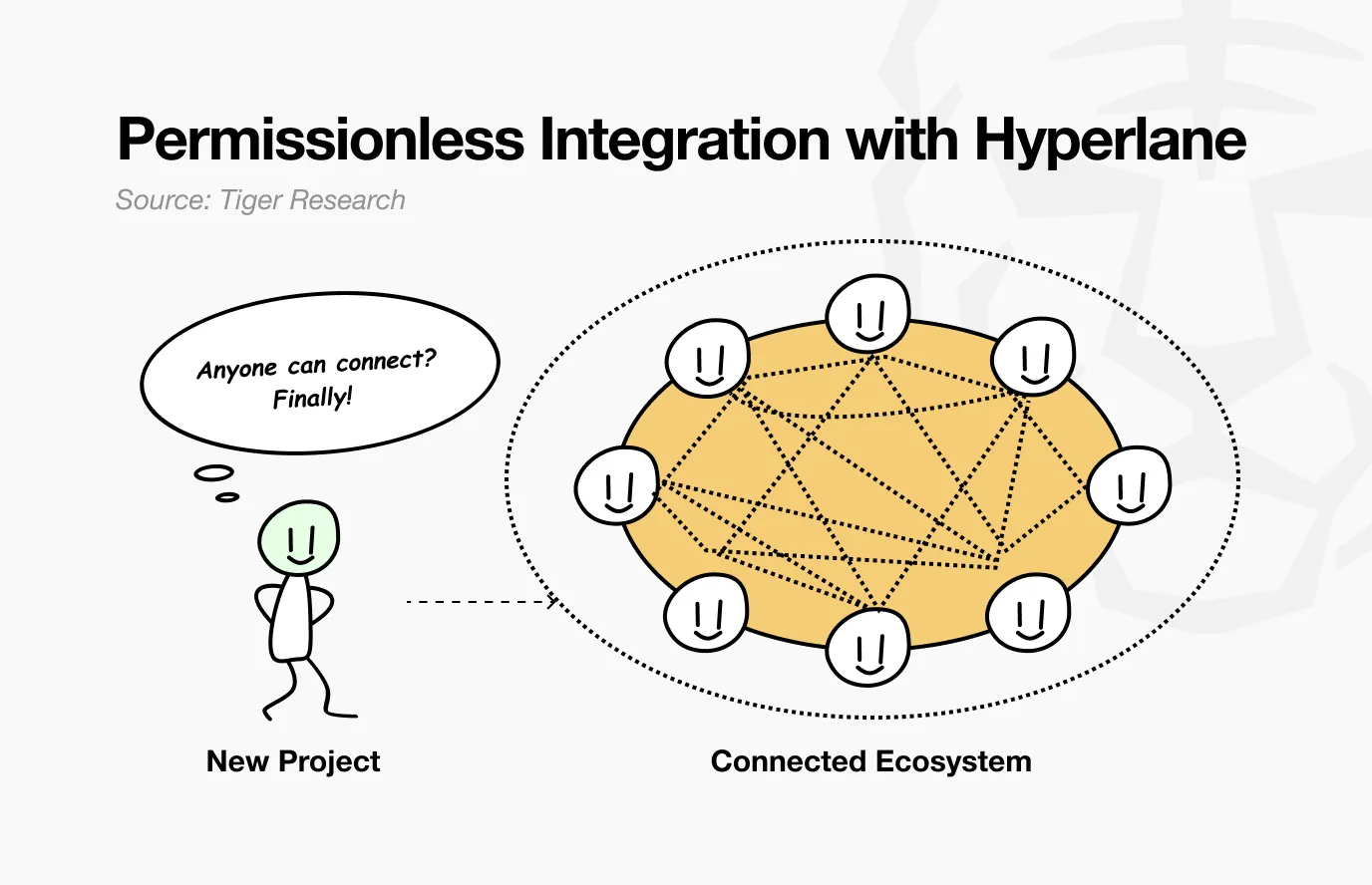
At the core of this architecture is a simple yet powerful principle: anyone can connect without permission, and any chain can be used as a destination without permission.
This model can be best understood through a familiar analogy - email. Just as anyone can send a message to any email address in the world without prior coordination, Hyperlane enables any blockchain with Mailbox installed to communicate with any other blockchain. It creates an environment where permissionless connectivity becomes the default state, something that is impossible with traditional approval-based systems.
2.2. Multiple Virtual Machine (VM) Compatibility

From the beginning, Hyperlane was designed with a modular architecture to support multiple virtual machine (VM) environments. It currently supports interoperability across Ethereum's EVM, CosmWasm based on Cosmos SDK chains, and Solana's SVM, and is adding support for Move-based chains.
Connecting different VM environments is inherently complex. Each blockchain operates with its own execution model, data structure, consensus mechanism, and asset standards. Achieving interoperability across these systems requires a highly specialized framework that can translate fundamentally different architectures.
For example, Ethereum’s EVM supports 18 decimal places, while Solana’s SVM uses 9. Overcoming even small differences while maintaining security and reliability is one of Hyperlane’s key technical achievements.
Hyperlane introduced "Hyperlane Warp Route" to solve the challenge of connecting different chains. Hyperlane Warp Route is a modular cross-chain asset bridge that supports permissionless token transfers between chains and supports the movement of various assets between different environments.
In short, Hyperlane Warp Routes operate according to the nature of the asset and the use case. Sometimes they operate like a vault, sometimes like a currency exchange, and sometimes like a direct wire transfer - each route type provides an appropriate method for each scenario. All of these processes run in different virtual machine environments using Hyperlane's inter-chain messaging.
-
Native Token Warp Routes: Supports direct cross-chain transfer of native fuel tokens (such as ETH) without wrapping.
-
Collateralized ERC20: Lock ERC20 tokens on the source chain as collateral for cross-chain transfers.
-
Synthetic ERC20: mint new ERC20 tokens on the target chain to represent the original token.
-
Multi-collateral Warp Routes: Allow multiple collateral tokens to provide liquidity.
-
Specialized Warp Routes: Add advanced features or integrate specific use cases (e.g. vaults, fiat-backed tokens).
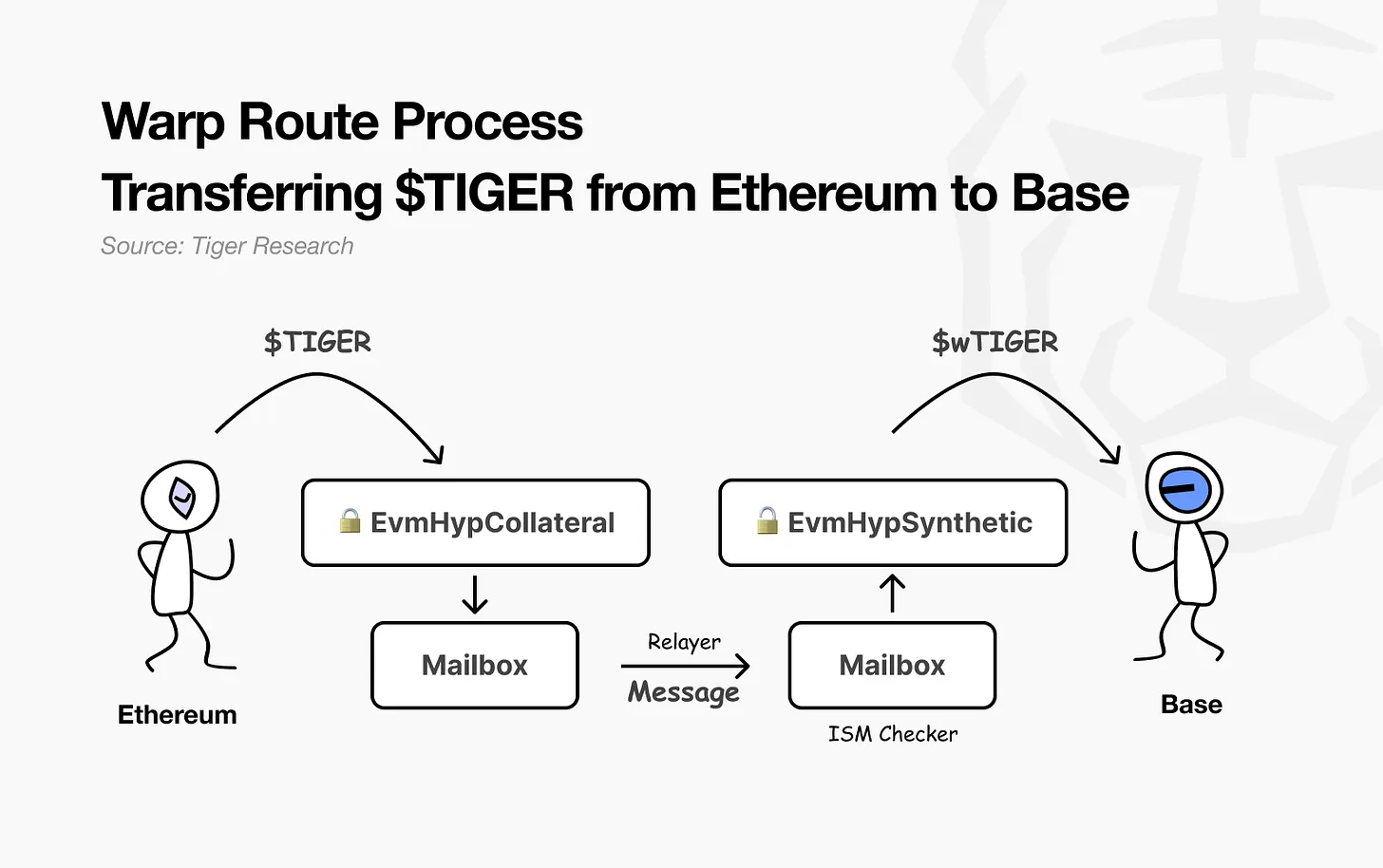
Let’s look at a real-world example using the lock-and-mint model. A developer named Ryan wants to move Tiger tokens ($TIGER) issued on Ethereum to the Base network.
Ryan first deploys a Hyperlane Warp Route contract on Ethereum and deposits $TIGER tokens into the contract (EvmHypCollateral). Then, the Ethereum Mailbox generates and sends a message instructing the Base network to mint a wrapped version of the Tiger token.
After receiving the message, the Base network verifies its authenticity using the Interchain Security Module (ISM). If the verification is successful, the Base network will mint wrapped Tiger tokens ($wTIGER) directly to the user's wallet.
Hyperlane Warp Route plays a key role in extending Hyperlane's vision of modular, permissionless interoperability for different chains. Developers only need to configure the contract according to the characteristics of each chain. The rest of the process - messaging, verification, and delivery - is handled by Hyperlane's infrastructure, enabling developers to connect across environments without having to deal with complex translation mechanisms.
2.3. Modular Security: Interchain Security Module (ISM)
While Hyperlane enables the seamless movement of messages and assets between chains — a key benefit for scalability — it also presents a key challenge: How can a receiving chain be confident that a message actually originated from where it claims to have come from? Delivering a message is one thing — verifying its authenticity is another.
To solve this problem, Hyperlane introduced the Interchain Security Module (ISM) - a modular security system that verifies the authenticity of a message before it is accepted on the target chain. ISM is an on-chain smart contract that verifies that the message was actually generated on the source chain, providing tamper-proof and provenance assurance.
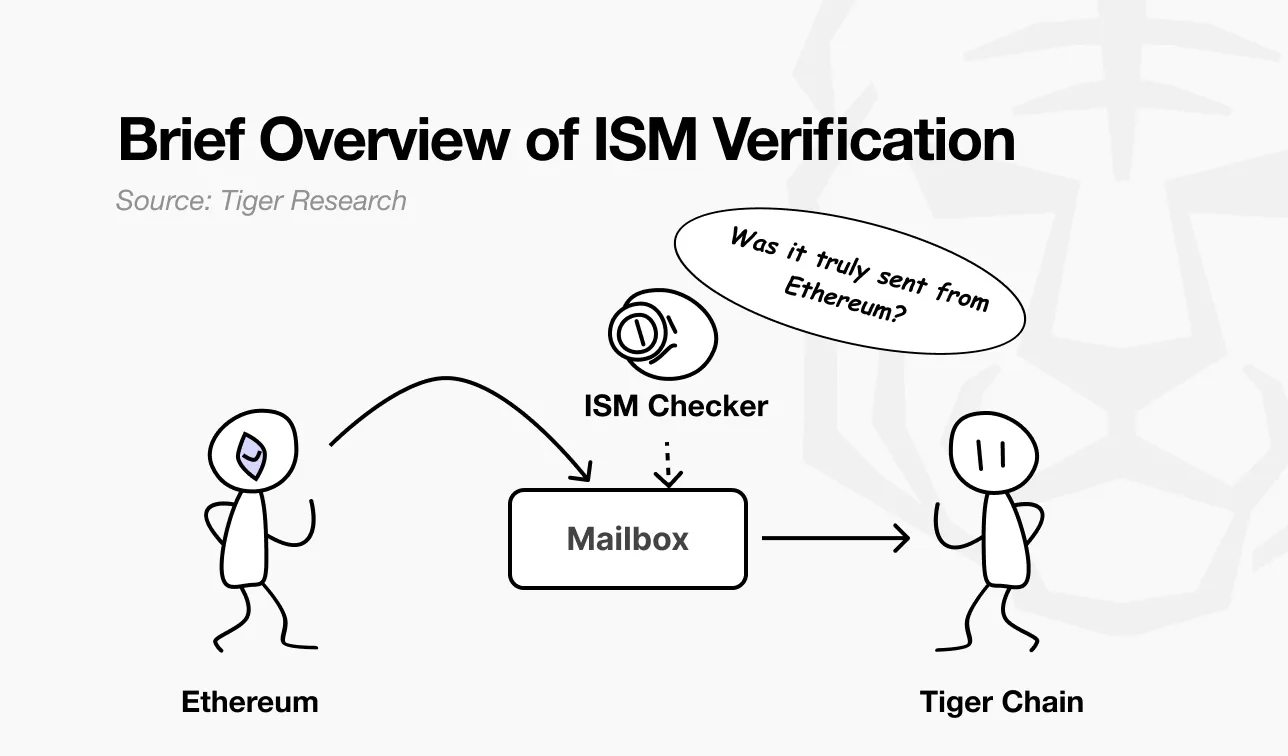
In short, when the target chain's Mailbox receives a message, it first asks: "Is this message really from the original chain?" Only after successful verification will the message be delivered to the intended destination. If the verification fails or looks suspicious, the message will be rejected.
The process is similar to how border control works when you travel internationally. Before you enter a country, immigration officials verify the authenticity of your passport—“Is this passport really issued by your home country?” Passports contain anti-counterfeiting features and cryptographic elements to prove their legitimacy. While anyone can forge a document, only those passports that can cryptographically prove their origin through proper verification will be accepted for entry.
Importantly, ISM can flexibly configure its security model based on the needs of the service. In practice, security requirements vary significantly by context. For example, a small token transfer may only require a basic validator signature for faster execution. In contrast, a multi-million dollar asset transfer may require a layered security approach - including Hyperlane validators, external bridges (such as Wormhole), and additional multi-signature verification.
In this way, the ISM framework reflects a key design decision: Hyperlane prioritizes connectivity and security through modular authentication. Applications can customize their security model while maintaining the permissionless nature of the protocol.
3. Developer Tools and Accessibility: The Easiest Way to Connect
Hyperlane prioritizes developer experience by providing a high level of accessibility and ease of use. Its command line interface (CLI) and TypeScript-based software development kit (SDK) are essential tools for integrating new chains into the Hyperlane ecosystem, sending inter-chain messages, and configuring Hyperlane Warp Route.
Both the CLI and SDK are completely open source and available for anyone to use. Developers can install the code from GitHub and start integrating without the need for a license agreement or approval process. The official documentation contains step-by-step tutorials that make it easy to get started even for developers with limited blockchain experience.
3.1. Hyperlane CLI: Direct tool integration
Hyperlane CLI is the official command line tool designed to allow developers to deploy and interact with Hyperlane contracts through simple command operations. It supports a wide range of operations - including deploying Hyperlane to a new blockchain, creating a Hyperlane Warp Route, and testing cross-chain messaging - usually with just one command.
-
Registration chain information: define the chain name, address and domain ID
-
Deploy core components: Automatically install Mailbox and ISM
-
Test Messaging: Send test messages between connected chains
3.2. Hyperlane SDK: Integration and Automation Toolkit
Hyperlane SDK is a TypeScript-based development toolkit that simplifies the implementation of inter-chain messaging. It enables developers to send messages, verify message status, and interact across chains with just a few lines of code.
Instead of writing custom logic for message routing or security verification, developers can leverage pre-built functions included in the SDK — such as “transferRemote()” for token transfers and “dispatch()” for message sending. It acts as a ready-made toolbox, accelerating integration and minimizing complexity.
The SDK plays a vital role in enabling Hyperlane’s permissionless design by enabling any application to quickly integrate inter-chain messaging. Just as payment APIs such as Stripe allow developers to add payment processing to their applications without having to build banking infrastructure, Hyperlane’s SDK makes blockchain-to-blockchain messaging easy to implement.
3.3. Hyperlane NEXUS: The simplest cross-chain bridge
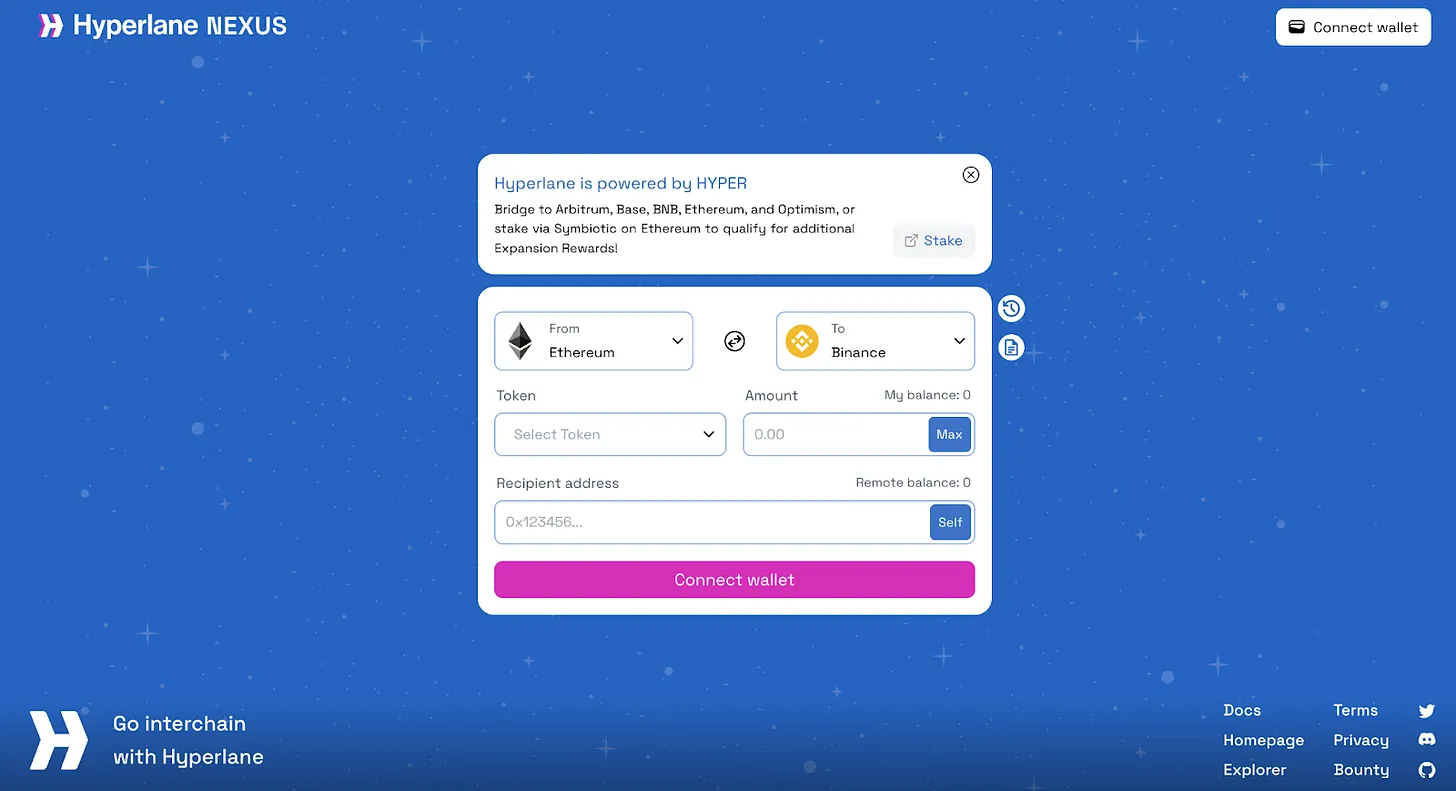
Source: Tiger Research
Non-developers can also experience the usefulness of Hyperlane through Hyperlane Nexus, a cross-chain bridge built on Hyperlane infrastructure. Hyperlane Nexus connects various blockchains (Ethereum, Solana, Eclipse, etc.) through a single interface, providing users with an accessible way to transfer assets between different chains using Hyperlane technology.
4. The future of Hyperlane
Hyperlane has demonstrated rapid growth since launching its testnet in late 2022. Originally named Abacus, the project was renamed Hyperlane in the fall of 2022 and began executing a dedicated ecosystem expansion strategy.
2023 is the foundational stage of Hyperlane's technical development. The team introduced a modular security stack that allows tailored security configurations based on the specific needs of each chain. At the same time, it implemented a permissionless deployment system that enables any developer to connect to a new chain without approval.
Significant efforts have also been made to improve the developer experience. Hyperlane simplifies the traditionally complex cross-chain communication process, making it easier to build intuitive multi-chain applications. Through integration with key projects such as Circle, the protocol has also achieved meaningful ecosystem expansion.
4.1. Prepare for accelerated growth
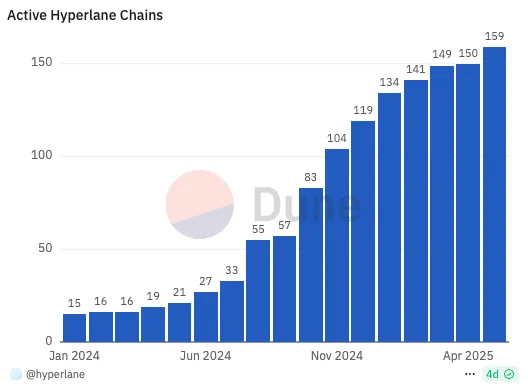
Source: Dune
Hyperlane currently supports over 150 blockchain networks, including Ethereum, Solana, and Avalanche. With billions of dollars in bridged assets, the protocol has clearly moved beyond the experimental stage and into commercial-scale deployment.
One of the most notable trends is the emergence of network effects. As more chains connect to Hyperlane, the incentive for others to join grows. New entrants gain instant access to the liquidity, user base, and interoperability of connected networks. Developers favor infrastructure that supports broad chain compatibility, while users seek greater utility and flexibility across assets.
Two core competitive advantages are driving Hyperlane’s growth:
-
Unrivaled connectivity across 150+ chains — more than any competitor.
-
The permissionless architecture significantly reduces access friction and accelerates ecosystem expansion.
Together, these advantages provide Hyperlane with a structurally superior growth trajectory compared to traditional interoperability solutions.
4.2. Giving $HYPER Practicality
With the launch of the HYPER token in April 2025, the main challenge for Hyperlane is to ensure the long-term utility of the token. The key question is whether HYPER can evolve from a speculative asset to a functional, integral part of the operation of the protocol.
Hyperlane first launched the "Expansion Rewards" program to ensure that users receive more rewards as they participate more in the ecosystem. The program allocates 25.5% of the total token supply and distributes $HYPER tokens every three months based on each user's protocol usage. Users accumulate points through activity, which are then converted into token rewards in proportion. The model functions much like a credit card rewards system - the more you use, the more rewards you get.
Two incentive mechanisms further reinforce this structure:
-
Chain Bonus: An additional 25% bonus is provided for transactions conducted on chains using Hyperlane as the primary bridge.
-
Long-Term Holding Bonus: Up to 60% additional bonus is provided to users who continue to hold the staked version of $HYPER (i.e. stHYPER).
The system is designed to reward high usage and long-term participation, effectively encouraging loyal users to become economic stakeholders in the growth of the protocol.
The goal of this incentive model is clear: the more users use the protocol and the longer they stay active, the bigger the rewards they receive. If this four-year program works as expected, it is expected to generate strong network effects throughout the Hyperlane ecosystem. These dynamics follow a self-reinforcing cycle:
-
Increased usage leads to more chains seeking integration
-
Network expansion creates a wider range of cross-chain options for users
-
More optionality accelerates the acquisition of new users
For a network like Hyperlane that is experiencing rapid chain scaling, this reward structure can significantly increase user satisfaction and serve as a catalyst for further growth.
However, a centralized utility model also presents risks. As $HYPER’s primary use case is closely tied to Hyperlane’s interoperability protocol, any decline in aggregate bridge demand or cross-chain activity could have a direct impact on token demand. Continuous monitoring of market conditions and usage trends will be critical.
Source: Symbiotic
Another core function of HYPER is network security. Users can stake HYPER to obtain stHYPER, a liquid staking token that supports the economic security of Hyperlane's default ISM. Validators (responsible for verifying the validity of cross-chain messages) receive staking rewards for correct verification. Conversely, if they sign invalid messages or engage in malicious behavior, their staked tokens will be slashed. This penalty is distributed among all stakers and used to compensate affected users.
Ultimately, the $HYPER token is designed to be more than just a transactional asset. By combining usage incentives, staking-based security, and long-term participation, it becomes a foundational component of the Hyperlane network. This architecture creates a self-reinforcing cycle:
-
More protocol usage leads to more $HYPER being distributed
-
More staking increases network security
-
Higher reliability attracts more users and chains to join
If this mechanism works as intended, $HYPER will play a core role in both network operations and security - supporting the sustainability and growth of the entire Hyperlane ecosystem.
4.3. Enhanced security
Perhaps most impressively, Hyperlane has maintained stable operations without major security incidents throughout its development, a record made possible by the stable management of its multi-signature validator group and a conservative approach to default configurations.
Strengthening security remains an ongoing priority. Through its bug bounty program, Hyperlane offers rewards of up to $2.5 million for identifying critical smart contract vulnerabilities. This has proven to be an effective mechanism to incentivize active participation by security researchers.
That being said, risks remain — especially given the open source and permissionless nature of the protocol. Continuous monitoring is necessary, especially as users’ independent customization of modules may introduce unforeseen vulnerabilities.
4.4. Becoming the core infrastructure of the interoperable Web3 era
As interoperability becomes a fundamental requirement for Web3, Hyperlane’s progress and potential take on greater significance. If its vision is realized, users will be able to interact with blockchain-based services without even having to think about which chain they are interacting with.
This represents a blueprint for a truly unified blockchain ecosystem. At this juncture, Hyperlane’s next moves will be key in determining the extent to which this vision can be realized.
You May Also Like

Watch Out: Numerous Economic Developments and Altcoin Events This Week! Here’s the Day-by-Day, Hour-by-Hour List

We are headed for ‘massive recession,’ and the ‘Fed is blind’, warns top economist
